Code Injection / Virus
Start Date: October 2023
Status: Completed as of December 2023
The project's objective is to create a virus that infects all executables in the target directory. When those executables are ran, the virus's payload runs before the normal program. Attempting to insert code into the main function of the ELF file will corrupt the ELF file and most likely causing it to seg fault. However, injecting it to a precise location and changing a few values in the ELF file as well, we can accomplish this goal.
Virus Payload
This virus contains a payload that will send an HTTP POST request to this web server. The web server logs the time and date in a database for users to view. Since we are not injecting anything besides the payload into the file we must write the assembly code for the functions we are using, specifically, write, connect, read, socket, and close. You can see all timestamps here. The last instruction of the payload jumps back to the start of the program, and begins to execute.
Virus Infection Method
In order to add the payload to the targeted file, we must first edit values within the ELF format that will allow both the virus to run while also preserving the original functionality of the program. First, we need to find a place to inject the code so that it doesn't interfere with any other segment. Most ELF files contain segments of executable code with amounts of room between the end of this segment and another segment. If there is enough virtual address space that fits the size of the payload we can inject it into this location. Most ELF files have sections padded with zeros following the data. This is due to the fixed sized of pages in page tables which are usually 4096 (0x1000) bytes. When the program gets loaded into memory its segments get loaded into pages within memory. Knowing this, we can inject the payload starting at the end of the last section loaded into the execution segment by changing the bytes, so they represent the correct instructions of the payload. Then, we change the memory size and file size of the execution segment so our payload also gets loaded into memory.
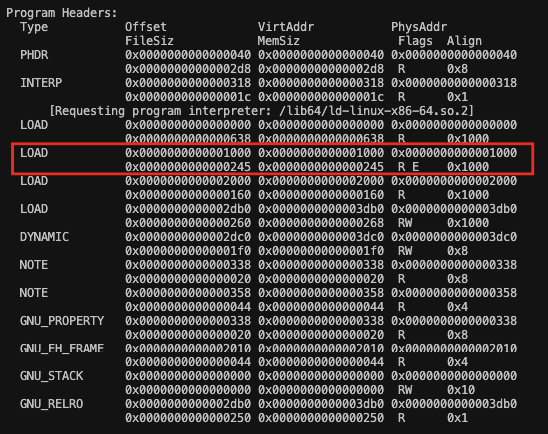
Here we see the segment that contains executable code. Its virtual address range is from 0x1000 to 0x1245. The next segment that gets loaded into memory begins at virtual address 0x2000 leaving 0xdbb space open which can hold the virus payload. Although this method relies on there being enough space, most files will have enough space to fit this virus as it is very small.

This is the last section that contains executable code. The end of the section is at 0x1245 which is where we will inject the code.
The last instruction of our payload needs to point to the original entry point of the infected file so we calculate this too.
length_of_code_injection = 0x27b
instruction_pointer = inject_offset + length_of_code_injection
jmp_to_start_operand = 0xffffffff + 1 - abs(OLD_ENTRY_POINT - instruction_pointer)Lastly, we change the entry point to point to the location of the payload.
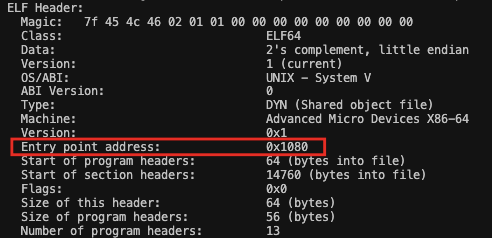
And we're done!
Installation
You can install the virus within a VM to run it by following these steps:
1. Install virtual box here
2. Install the VM that contains the virus here
3. Open virtual box and select File -> Import Appliance, then select the download VM, select Next and then Finish.
4. Open the VM
5. Open the terminal
6. Type 'sudo su' followed by the password 'ubuntu'
7. Type 'cd ELF-Code-Injection'
Now that you are in the directory with the virus, inject.py, feel free to add any ELF file to this directory for testing. When you want to run the virus and infect all ELF files in the current directory type 'python3 inject.py.' Then try running the ELF files.
Timestamps
You can view the timestamps to see all times the injected code ran successfully in an effected file. Try running the virus in the provided VM, run an effected file, and then view the timestamps page to see when the effective file was ran.