Geo-Spoofing Detection
GitHub Source CodeStarted: June 2021
Status: Completed as of August 2021
This project was the main part of my experience at the 2021 REU at the University of Houston.
Research Problem
Geo-Spoofing occurs when someone connects to a VPN to disguise their location when connecting to a server. This can be a huge problem for media sharing companies such as Netflix that have different content in each reason. In this project myself as well as other researchers at the University at Houston tackle this issue.
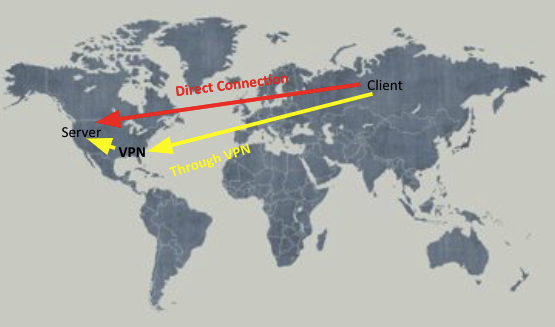
Hypothesis
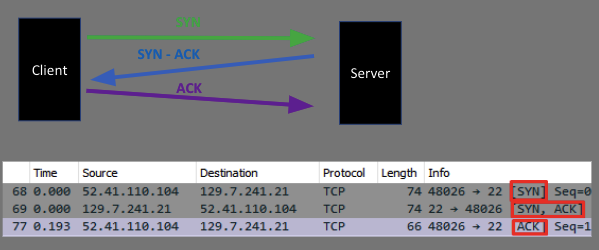
We will be testing connections to a server via SSH. Upon a client's connection to a server the TCP threeway handshake is performed. We can capture the Round Trip Time on the server. Using a probing method (either initiating a TCP connection or pinging the client) we can find a disparity in the Round Trip Times in order to determine if the client is connecting through a VPN.
Experiment
To set up our experiment we launched instances on AWS across the world in locations such as South Korea, Germany, and the United States. Instances were either clients, VPNs, or servers. Our experiment included 84 VPN cases vs. 66 direct cases. We are testing to see if our methods of detection either through different or ratio of the two round trip times yield high true positive and low false negative results.
Using PyShark, a Python wrapper for tshark (Wireshark), we are able to read incoming packets and perform live analysis on them on the server. The script follows the below psuedocode.
IF packet has SYN flag AND sent to server
store client IP address [i]
IF packet has SYN ACK flag AND sent from server
store time packet was sent associate with [i]
IF packet has ACK flag AND sent to server
store time packet was received associate with [i]
calculate Round Trip Time (time received - time sent)
store RTT time associated with [i]
PROBE (send SYN packet to [i])
### Round Trip Time of Probing packet
IF packet has SYN flag AND sent from server
store time packet was sent associate with [i]
IF packet has SYN ACK flag AND sent to server
store time packet was received associate with [i]
calculate probe Round Trip Time (time received - time sent)
store probe RTT time associated with [i]
IF probe RTT - initial RTT < 0.01s
client is DIRECT CONNECTION
ELSE
client is USING VPNResults
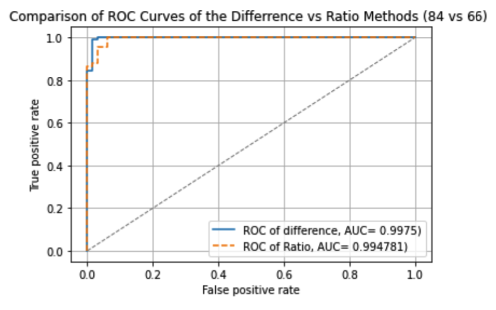
These results show there is high chance >99% that we are able to distinguish between true positives and false positives with both the ratio and difference method.
Future Work
In our tests we rely on certain services to be open such as port 22 for SSH. If this service is disabled we are unable to use our methods to get a probing Round Trip Time. Other methods on finding Round Trip Time should be explored in order to maximize the probability at least one service would be active on the client's end.